Parler
Parler Gab
Gab
Is Pushwoosh committing fraud by falsely claiming it is U.S.-based in regulatory filings?
At the very same time, Pushwoosh claims to be a U.S. company, both on social media and more importantly in U.S. regulatory filings, the latter of which appears to constitute fraud. At various times, Pushwoosh has made conflicting claims about where in the U.S. it is supposedly located. When not claiming to be based in D.C., the company has said it is based in Maryland, while at another point in time it claimed to be based in California. These revelations are particularly concerning in light of the fact that Pushwoosh's role in code development involves creating software tools for developers that allow for the monitoring and surveillance of smartphone app users' online activity. Clients of Pushwoosh are able to use this information to send custom-made push notifications to smartphone app users' devices straight from the company's servers. On its website, Pushwoosh claims that none of the information it collects is sensitive in nature. Reuters agrees with this, claiming it found no evidence that Pushwoosh in any way mishandled user data. The problem with all this, though, is that the Russian government requires companies like Pushwoosh to hand over collected data to domestic security agencies. This means the Kremlin likely has a trove of data at its disposal about various things that are happening at the CDC, in the Army, and elsewhere. In an emailed statement to Reuters, Pushwoosh founder Max Konev said he has never tried to mask his company's Russian origins, despite how things appear. "I am proud to be Russian and I would never hide this," he said. Following the publishing of the Reuters exposé, Pushwoosh published a blog post aimed at dispelling the idea that it is a Russian company in disguise. "Pushwoosh Inc. is a privately held C-Corp company incorporated under the state laws of Delaware, USA," the post explains. "Pushwoosh Inc. was never owned by any company registered in the Russian Federation." More of the latest news can be found at CyberWar.news. Sources for this article include: Reuters.com NaturalNews.comFTX contagion spreads as BlockFi crypto firm files for Chapter 11 bankruptcy
By Ethan Huff // Share
Fauci, Jha urge Americans to get their bivalent COVID-19 vaccine booster shots
By Belle Carter // Share
Live with Dr. Jane Ruby: Sasha Latypova exposes unsanitary COVID-19 vaccine manufacturing facility
By Belle Carter // Share
Jim Caviezel blasts Hollywood bigwigs for horrific acts done on children to extract adrenochrome
By Belle Carter // Share
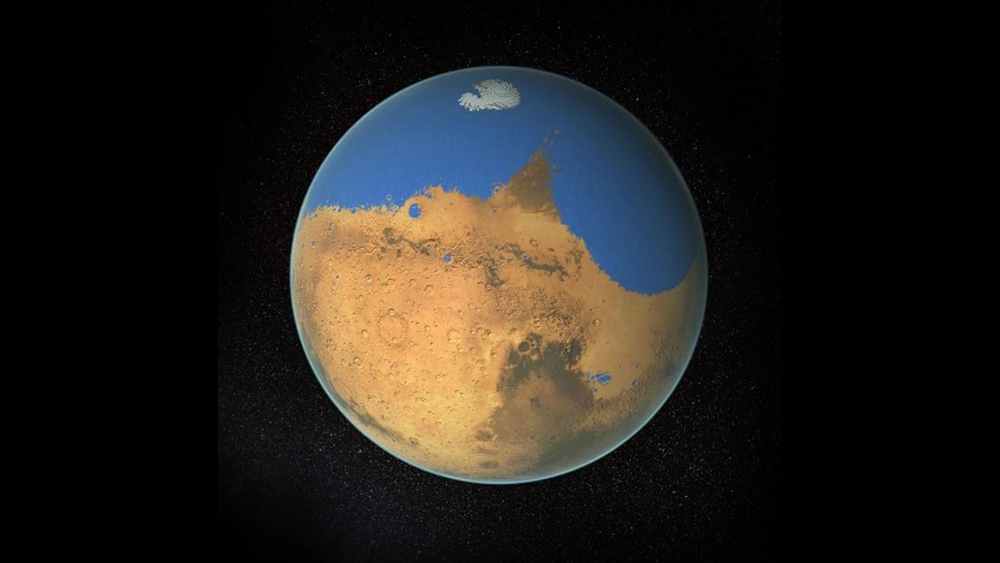
Study: Mars was covered by deep oceans 4.5 billion years ago
By Kevin Hughes // Share
Governments continue to obscure COVID-19 vaccine data amid rising concerns over excess deaths
By patricklewis // Share
Tech giant Microsoft backs EXTINCTION with its support of carbon capture programs
By ramontomeydw // Share
Germany to resume arms exports to Israel despite repeated ceasefire violations
By isabelle // Share